Event Log Manager (ELM)
Efficiently manage massive data flows
Become a reseller
In business since 2004, blësk has entered the market as the solution of choice for network monitoring.

Key advantages
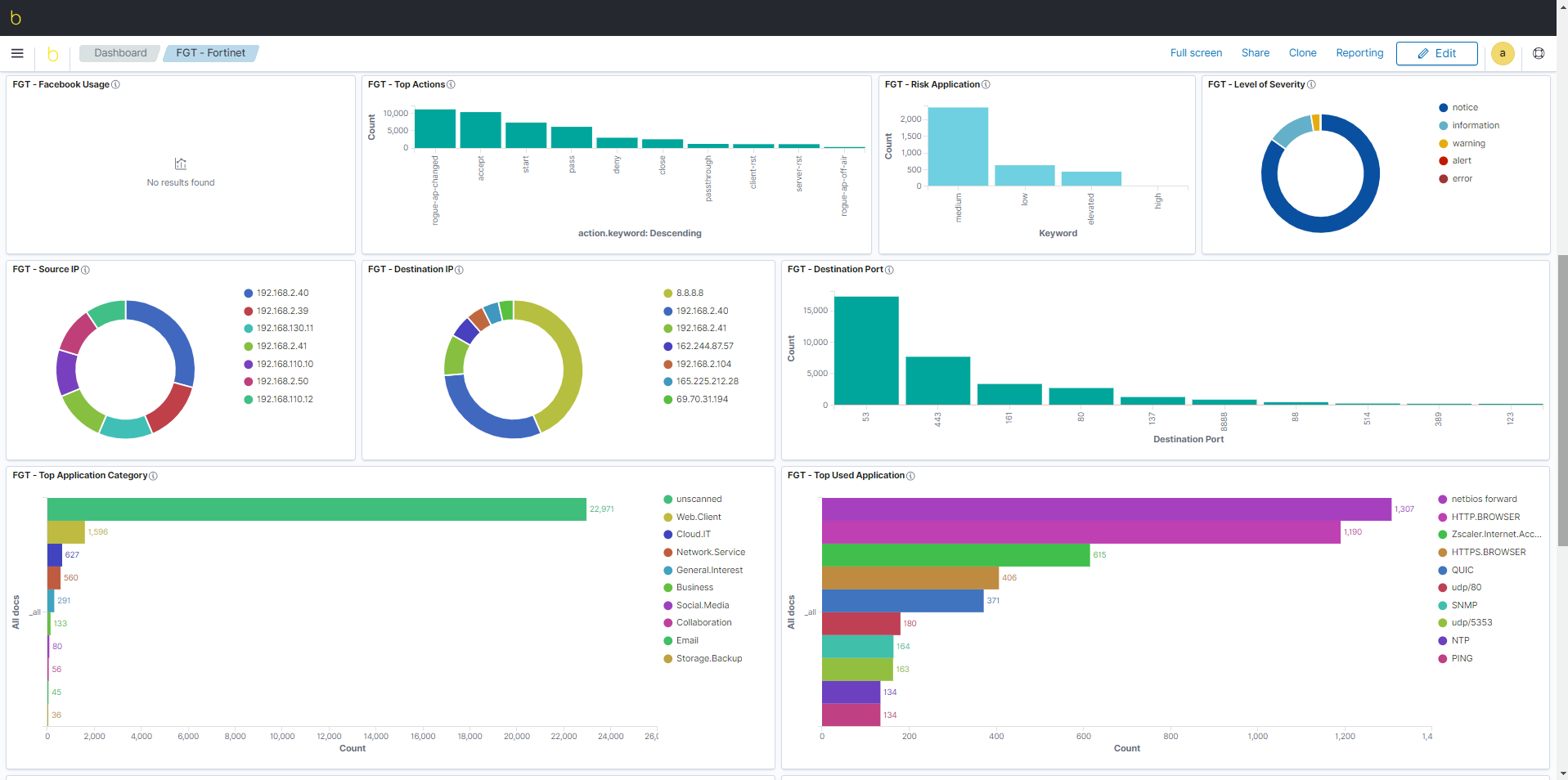
- Creating customize dashboards
- Archiving your system events for years
- Combining many types of searches
- Quick searches in billions of entries
With all the log events generated by your systems, it is easy to get lost and miss out on what is really important. Not being able to sort and focus quickly on issues can too often affect systems functionality. In order to gain complete visibility of your log entries and to act on hidden issues, you need a robust log aggregation solution.
blësk Event Log Manager (ELM) allows you to quickly identify useful information from the syslogs received. ELM is a flexible and powerful tool that helps your team sort the flow of data to quickly detect and act on problems before damage occurs.
Try a solution that identifies your problems, and watch everything happen in real time.
SIEM Market According to Gartner
Gartner defines the Security Information and Event Management (SIEM) market based on the customer’s needs to analyze real-time event data in order to quickly detect targeted attacks and data breaches. It also takes into account the need to collect, store, search, and log data for incident response and regulatory compliance.

blësk ELM, your enterprise SIEM
blësk ELM allows you to keep an eye on all your logs to ensure security. Take data from any source, in any format, and perform collection, normalization, indexing, real-time search and event analysis from your machines, systems, and applications (firewalls, IDS/ISP, Network Machines, Security Machines, Applications, Databases, servers, directories, IAM). Monitor applications, user behaviors, and data access to detect anomalies.
In summary, blësk ELM is a flexible and powerful tool that can store billions of log entries, filter with an intelligent search and create tables that allow better visualization of log events (syslog). This tool helps you:
-
Centralize all your system events;
- Enrich your analyses;
- Detect “zero-day” vulnerabilities;
- Detect malicious codes;
- Perform rapid searches.